
Portail des élèves de maternelle au cycle 2 : Annuaire collaboratif à partir duquel il est très simple de créer et gérer sa propre sélection. >>>

Portail des élèves de cycle 3 : Annuaire collaboratif + espaces personnalisables qui permettent aux enseignants de créer et gérer leurs propres pages de liens >>>

Sélection d'activités mathématiques au format Flash, classées par domaines, destinées aux élèves de maternelle et d'élémentaire >>>

Les pragmactivités sont des applications Web responsives, multiplateformes, compatibles avec tous les navigateurs récents, conçues pour les écoles maternelle et élémentaire. >>>

Application Web permettant de consulter et de créer des livres numériques de 8 pages qui peuvent être imprimés dans trois formats. Des jeux interactifs sont générés automatiquement à partir du contenu du livre. >>>

Application Web permettant de coder ou décoder des déplacements sur quadrillage, afin de construire ses propres parcours scénarisés, de créer des albums multimédia, de dessiner, tout en s'initiant à l'algorithmie. >>>

Application Web permettant de s'entraîner, dans plusieurs langues, à poser et à répondre à 9 questions qui peuvent caractériser un personnage. >>>

Application Web pédagogique multijoueur qui permet de s'entraîner à mémoriser et à analyser des mots pour bien les orthographier. >>>
Application Web multimédia, gratuite et téléchargeable, qui permet via l'apprentissage ritualisé d'un ou deux mots par jour, de découvrir et de réinvestir du vocabulaire et de sensibiliser les élèves à la lecture-écriture. >>>
Générateur de quiz pour l'école, multimédia, multijoueur, qui propose plusieurs activités à partir d'un même quiz, et peut adapter les questions en fonction des réponses de l'apprenant. >>>
Enregistreur MP3 qui permet de créer un même enregistrement à partir de plusieurs prises de son consécutives.>>>
Application Web qui permet d'afficher une série d'images dans une page Web, en local, sans connexion Internet, accompagnées ou non d'un son, en mode grille ou en mode diaporama. >>>

Application Web qui permet de générer des visages afin d'exprimer des émotions, en cliquant sur les parties du visage ou sur des onglets les représentant. >>>

Application Web qui permet de lire une bande dessinée en anglais pour découvrir un objet disparu, tout en découvrant 10 monuments célèbres de pays anglophones. >>>

Application Web qui permet de créer des grilles de tableau bavard, et de générer automatiquement des activités interactives et des supports imprimables à partir des grilles créées. >>>
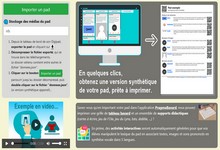
Application Web qui permet de générer une document synthétique imprimable à partir d'un export de Digipad. >>>
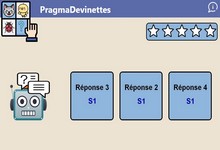
Application Web qui permet de générer des devinettes multimédias. Elle est utilisable sans connexion Internet. >>>
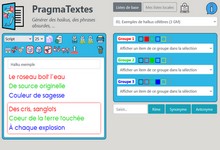
Application Web qui permet de générer des textes poétiques, humoristiques, ... et de les modifier, les exporter et les écouter en synthèse vocale. >>>
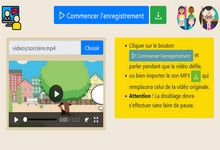
Application Web qui permet de remplacer la bande audio d'une vidéo par son propre son, via une interface minimaliste utilisable par des enfants. Il ne s'agit pas d'un outil de montage vidéo... >>>

Application Web qui permet de reconstituer une carte postale mosaïque d'une dizaine d'espaces naturels de pays anglophones, en retrouvant notamment les animaux et les plantes qui les caractérisent. >>>
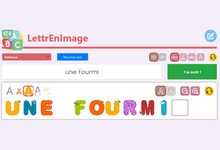
Application Web qui permet de saisir des lettres qui s'affichent sous forme d'images. En se référant à des listes de mots disponibles ou à créer, les élèves peuvent écrire ou recopier des mots, tout en validant leur saisie. >>>

Application Web qui propose une batterie d’outils facilitant l’exploitation des TNI et ENI, voire à défaut, des vidéo-projecteurs. >>>

Portail des vidéos de pratiques de classe : Sélection de vidéos de situations pédagogiques qui intègrent l'usage du numérique, accompagnées de témoignages d'élèves et d'enseignants qui les ont vécues >>>

Panorama synthétique des usages du numérique à l'école primaire (enjeux et perspectives, pistes pédagogiques, présentation d'outils, tutoriels, ... ) >>>

Plus de 1 000 ressources pour l'école (attention ! 2005) : Les TICE pour quoi faire et comment faire ? Débuter avec l'ordinateur - Mettre en oeuvre le B2i - Installer des logiciels et des polices d'écriture >>>
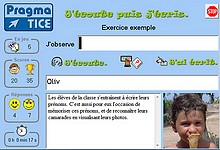
Exerciseur multimédia original dans lequel l'élève s'entraîne à saisir précisément un mot, une expression ou un nombre après l'écoute d'un message sonore, en s'aidant d'une image et/ou d'un texte d'accompagnement >>>
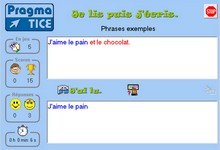
Exerciseur pour écrire sans erreur dans lequel l'élève s'entraîne à saisir précisément une réponse (mot, expression, phrase, nombre, etc...) en respectant une consigne >>>
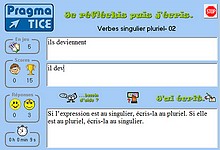
Exerciseur pour saisir les bonnes réponses dans lequel l'élève s'entraîne à saisir précisément une réponse (mot, expression, phrase, nombre, etc...) en respectant une consigne >>>
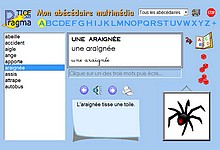
Logiciel dans lequel l'élève consulte des abécédaires personnalisables (image, son, écriture dans trois polices) et s'entraîne à recopier les mots. Une affiche A4 peut être imprimée pour chaque mot >>>
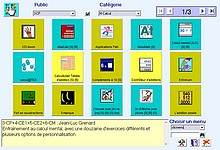
Interface graphique personnalisable et évolutive, conçue pour lancer en toute sécurité des logiciels et documents >>>

Série d'applications interactives pour l'école publiées sur le site Informatique-Enseignant.com, comprenant des options qui permettent d'adapter les activités au niveau de la classe >>>

Logiciels de Maths & Français pour cycle 3, compatibles Windows 10 et antérieurs, adaptés à un travail individualisé >>>

Interface paramétrable occupant l'ensemble du bureau de l'utilisateur, qui permet d'accéder à de nombreux logiciels en un seul clic. >>>